
Tripwire Security Configuration Management
Helps organizations of all shapes and sizes successfully automate the hardening of their servers
|
Real-time change audit and threat detection, compliance policies and business context visibility reduces security risk |
Collect all of the "who", "what", and "when" data on change and threat indicators |
Agentless monitoring for compliance and policy increases security for your network infrastructure devices |
Overview:
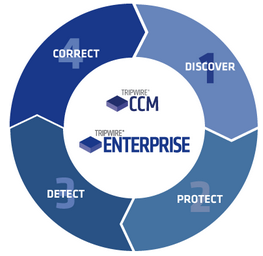
Tripwire Continuous Security Configuration Management Solutions
Tripwire helps organizations of all shapes and sizes successfully automate the hardening of their servers, databases and network devices. Our patented, award winning suite of Security Configuration Management (SCM) products, services and solutions then continuously monitors the integrity of those systems.
SCM is one of the most effective and cost-effective security controls you can implement, and it’s foundational to many regulatory standards and security frameworks. Tripwire Enterprise and Tripwire CCM provide best-in-class SCM so you can measurably reduce your infrastructure’s attack surface while improving your security posture. And our next-generation approach delivers it continuously at the speed of change and in context of your business for total visibility of your risk.
- Discover -Find all networked devices: ports, protocols, services, applications, vulnerabilities, operating systems
- Protect - Harden systems through automated configuration assessment: PCI, SOX, NERC, HIPAA, SANS 20 CSC, CIS, NIST, DISA STIGs, ISO, COBIT
- Detect – Continuous, real-time integrity monitoring: agent or agentless, integrated File Integrity Monitoring (FIM)
- Correct – Remediation guidance and implementation
How Can Tripwire's SCM Solutions Help?
- Significantly reduces the attack surface with an end-to-end continuous SCM solution for policy management, integrity monitoring and change auditing.
- Delivers a scalable, automated way to ensure system integrity and continual system hardening of enterprise systems and continuously monitors all change to alert on changes of interest.
- Achieves and maintains a known, trusted state to reduce risk, prevent audit failures by complying with standards, and assures high availability.
- Integrates with SIEMs, IT-GRC platforms, and change management processes and tools to provide system state intelligence.



