
Tripwire Compliance
Reduce Costs and Maintain IT Regulatory Compliance with Automation
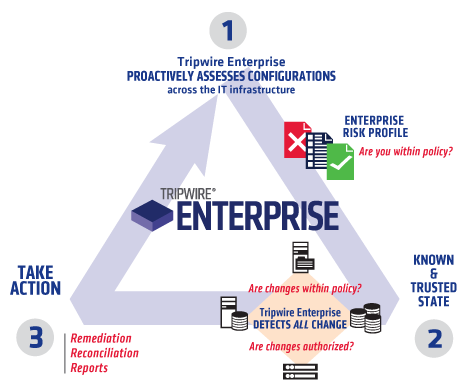
Overview:
The ever-increasing number and sophistication of threats has placed unprecedented pressure on information security managers, forcing them to meet external regulatory compliance requirements or internal security mandates in order to protect their businesses. Unfortunately, many organizations achieve compliance through last-minute heroics to generate proof of controls for auditors. This moment-in-time approach to compliance increases the workload and costs, yet provides little protection from IT security threats.
Make IT Regulatory Compliance Operational
Whether you have one or several compliance initiatives to respond to, Tripwire solutions automate the assessment of IT controls and provides a streamlined way to remediate non-compliant settings. This means that maintaining continuous compliance becomes a minor part of your daily operations — instead of separately managed projects that provide only temporary compliance and the illusion of security.
Tripwire NERC Solution Suite:
AUTOMATE AND SIMPLIFY COMPLIANCE
The North American Electric Reliability Corporation (NERC) maintains comprehensive reliability standards that define requirements for planning and operating the bulk electric system. Among these are ten Critical Infrastructure Protection (CIP) Cyber Security Standards, which specify a minimum set of controls and processes for power generation and transmission companies to follow to ensure the security of the North American power grid.
The Tripwire NERC Solution Suite provides a comprehensive solution for NERC CIP compliance by offering a tailored combination of standard products, now including IP360 (vulnerability management), Tripwire Enterprise (security configuration management), and Tripwire Log Center (intelligent event logging), NERC-specific extensions and industry-experienced consultants.
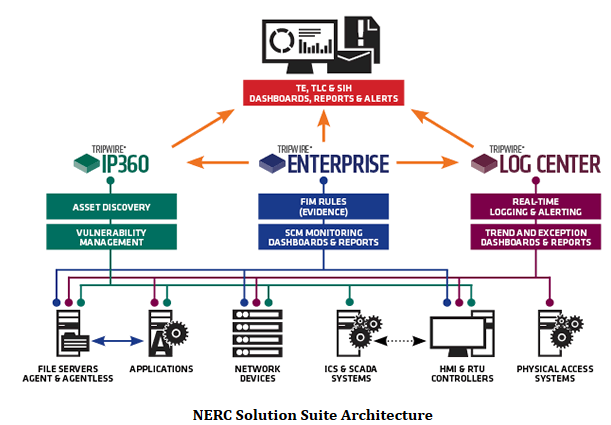
Tripwire enables registered entities to achieve and maintain NERC CIP compliance by:
- Asset Discovery - Tripwire can scan your network and auto-discover the assets you have, saving hours of manual effort, and increasing trust in the identification of systems and software in your environment
- Continuous Monitoring - continuously collect detailed status information on all your critical cyber assets and immediately detect any changes
- Automated Assessment - automatically aggregate and analyze your security data and alert on suspicious events or modifications that impact your compliance status
- Audit-ready Evidence - quickly generate reports and dashboards that fully document, by CIP requirement, your compliance with security controls and processes
Tripwire Coverage of NERC CIP Requirements
With the NERC Solution Suite, Tripwire can help power companies automate 19 of the 32 requirements contained in the NERC CIPv5 standards. Tripwire gets you ready for v3 or v5 today, and will help prepare you for whatever revisions may come tomorrow. Click below to see how Tripwire addresses some of the toughest technical controls within each specific CIP requirement.
| CIP-002 R1: BES Cyber System Identification and Categorization | ||
|---|---|---|
| CIP Requirement | Description | How Tripwire can help1 |
| CIP-002 R1: BES Cyber System Identification | Each Responsible Entity shall implement a process that considers each of the following assets for purposes of parts 1.1 through 1.3:
|
Tripwire IP360 combined with professional services use of Tripwire discovery tools can help identify and track the critical cyber assets that are in scope.
Tripwire IP360 can discover all assets in assigned IP scope using TCP and UDP protocols. Discovery of all assets allows for further classification and interegation. |
| CIP-002 R2: Regular Approval | The Responsible Entity shall:
|
|
| CIP-003: Security Management Controls | ||
| CIP-003 R1: Cyber Security Policy for High/Medium Systems | Each Responsible Entity, for its high impact and medium impact BES Cyber Systems, shall review and obtain CIP Senior Manager approval at least once every 15 calendar months for one or more documented cyber security policies that collectively address the following topics:
|
|
| CIP-003 R2: Cyber Security Policy for Low Systems | Each Responsible Entity for its assets identified in CIP-002-5, Requirement R1, Part R1.3, shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented cyber security policies that collectively address the following topics, and review and obtain CIP Senior Manager approval for those policies at least once every 15 calendar months:
|
Tripwire validates and monitors security settings and related configurations to ensure that monitoring of dial-up services and features has been implemented.
Tripwire reports can provide excellent forensic details to assist in the investigation/analysis of an Incident or in the preparation/evaluation of an IOC report. |
| CIP-003 R3: Identification of Senior Manager | Each Responsible Entity shall identify a CIP Senior Manager by name and document any change within 30 calendar days of the change. | |
| CIP-003 R4: Delegation of Authority | The Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, a documented process to delegate authority, unless no delegations are used. Where allowed by the CIP Standards, the CIP Senior Manager may delegate authority for specific actions to a delegate or delegates. These delegations shall be documented, including the name or title of the delegate, the specific actions delegated, and the date of the delegation; approved by the CIP Senior Manager; and updated within 30 days of any change to the delegation. Delegation changes do not need to be reinstated with a change to the delegator. | |
| CIP-004: Training and Personnel Security | ||
| CIP-004 R1: Awareness | Each Responsible Entity shall implement one or more documented processes that collectively include each of the applicable requirement parts in CIP-004-5 Table R1 – Security Awareness Program.
R1.1. Security awareness that, at least once each calendar quarter, reinforces cyber security practices (which may include associated physical security practices) for the Responsible Entity’s personnel who have authorized electronic or authorized unescorted physical access to BES Cyber Systems. |
|
| CIP-004 R2: Training | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, a cyber security training program(s) appropriate to individual roles, functions, or responsibilities that collectively includes each of the applicable requirement parts in CIP-004-5 Table R2 – Cyber Security Training Program.
R2.1. Training content on:
R2.2. Require completion of the training specified in Part 2.1 prior to granting authorized electronic access and authorized unescorted physical access to applicable Cyber Assets, except during CIP Exceptional Circumstances. |
|
| CIP-004 R3: Personnel Risk Assessment Program | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented personnel risk assessment programs to attain and retain authorized electronic or authorized unescorted physical access to BES Cyber Systems that collectively include each of the applicable requirement parts in CIP-004-5 Table R3 – Personnel Risk Assessment Program.
R3.1. Process to confirm identity.
|
|
| CIP-004 R4: Access Management Program | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented access management programs that collectively include each of the applicable requirement parts in CIP-004-5 Table R4 – Access Management Program.
|
Tripwire Enterprise and Log Center is used to verify account and access control settings on systems and networks via logs and configuration changes.
Tripwire's FIM whitelist profiler extension can verify only approved accounts exist on systems, as codified in an authorized user whitelist. |
| CIP-004 R5: Access Revocation Program | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented access revocation programs that collectively include each of the applicable requirement parts in CIP-004-5 Table R5 – Access Revocation.
|
Standard monitoring access logs comes out of the box with Tripwire Log Center; access controls are monitored by TE, and tailored rules can be created to search for access control logs that match lists of former employees to validate that access and activity by the former employees has been stopped.
Tripwire's FIM whitelist profiler extension can verify only approved accounts exist on systems, as codified in an authorized user whitelist. Tripwire can help ensure that shared accounts have suitable controls, and that passwords have been changed according to stated policies. |
| CIP-005: Electronic Security Perimeter(s) | ||
| CIP-005 R1: Electronic Security Perimeter | Each Responsible Entity shall implement one or more documented processes that collectively include each of the applicable requirement parts in CIP-005-5 Table R1 – Electronic Security Perimeter.
|
Tripwire IP360 combined with professional services use of Tripwire discovery tools can help identify and track the cyber assets that are in scope. |
| CIP-005 R2: Interactive Remote Access Management | Each Responsible Entity allowing Interactive Remote Access to BES Cyber Systems shall implement one or more documented processes that collectively include the applicable requirement parts, where technically feasible, in CIP-005-5 Table R2 – Interactive Remote Access Management.
|
Tripwire Change Auditing and Configuration Assessment/reporting will track settings associated with authenticated access control for remote use.
Tripwire validates and monitors security settings and configurations made to ensure strong authentication by external interactive users. |
| CIP-006: Physical Security of BES Cyber Systems | ||
| CIP-006 R1: Physical Security Plan | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented physical security plans that collectively include all of the applicable requirement parts in CIP-006-5 Table R1 – Physical Security Plan.
|
Tripwire can facilitate monitoring of physical access and other environmental monitoring systems through automated collection and analysis of these device logs by Tripwire Log Center.
Tripwire can facilitate monitoring of physical access and other environmental monitoring systems by analyzing the logs collected, utilizing custom correlation rules to alert on unauthorized access attempts. Tripwire can facilitate monitoring of physical access and other environmental monitoring systems through automated collection and analysis of these device logs by Tripwire Log Center.Tripwire can facilitate monitoring of physical access and other environmental monitoring systems by analyzing the logs collected, utilizing custom correlation rules to alert on unauthorized access attempts. |
| CIP-006 R2: Visitor Control Program | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented visitor control programs that include each of the applicable requirement parts in CIP-006-5 Table R2 – Visitor Control Program.
|
Log retention for the required periods can be assured through Tripwire's log management and archiving capabilities. |
| CIP-006 R3: Maintenance and Testing Program | Each Responsible Entity shall implement one or more documented Physical Access Control System maintenance and testing programs that collectively include each of the applicable requirement parts in CIP-006-5 Table R3 – Maintenance and Testing Program.
R3.1. Maintenance and testing of each Physical Access Control System and locally mounted hardware or devices at the Physical Security Perimeter at least once every 24 calendar months to ensure they function properly. |
|
| CIP-007: Systems Security Management | ||
| CIP-007 R1: Ports and Services | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented processes that collectively include each of the applicable requirement parts in CIP-007-5 Table R1 – Ports and Services.
|
Tripwire's FIM whitelist profiler extension can monitor ports and services and compare current state against a tailored set of customer-specific approved port and services, alerting when monitoring detects a variance.
Tripwire's FIM whitelist profiler extension can monitor ports and services and compare current state against a tailored set of customer-specific approved port and services, alerting when monitoring detects a variance. Tripwire can detect whether removeable media has been connected to a monitored system, providing timely alerting to potential violations. |
| CIP-007 R2: Security Patch Management | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented processes that collectively include each of the applicable requirement parts in CIP-007-5 Table R2 – Security Patch Management.
|
Tripwire's FIM whitelist profiler extension can identify software versions and installed patches and compare current state against a tailored set of customer-specific approved software versions and patches, alerting when there is a variance on specific BCA's.
IP360's vulnerability assessment capabilities can identify any necessary patches that should be installed on a broad range of BCA systems based on vendor recommendations. The vulnerability database is typically updated every week. Tripwire detects when patches are implemented and will record this information for later review and analysis. |
| CIP-007 R3: Malicious Code Prevention | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented processes that collectively include each of the applicable requirement parts in CIP-007-5 Table R3 – Malicious Code Prevention.
|
Tripwire can scan for anti-virus and malware products installed through tailored change auditing rules. Logs can be watched to find specific malware events and allow the Tripwire operator to examine the device for incident information.
Tripwire's FIM monitoring can detect the introduction of unapproved/unauthorized files on a given system. Tripwire checks for security settings and configurations to validate anti-virus and malware prevention is enabled and updated appropriately. |
| CIP-007 R4: Security Event Monitoring | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented processes that collectively include each of the applicable requirement parts in CIP-007-5 Table R4 – Security Event Monitoring.
|
Tripwire supports technical and procedural processes to validate and monitor security events on cyber assets.
Tripwire Log Center rules can capture successful and unsuccessful logins for all monitored hosts, and provide alerting as desired. Tripwire Log Center rules can detect and alert when a BCA stops logging activity, thus providing alerting on continuous 24x7 basis.Log retention for the required periods can be assured through Tripwire's log management and archiving capabilities. Log retention for the required periods can be assured through Tripwire's log management and archiving capabilities. |
| CIP-007 R5: System Access Controls | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented processes that collectively include each of the applicable requirement parts in CIP-007-5 Table R5 – System Access Controls.
|
Tripwire can scan logs for account management activity and configuration settings for changes to account privilege, alerting as appropriate.
Tripwire can scan logs for account management activity and configuration settings to ensure authentication is enforced, alerting as appropriate. Tripwire's FIM whitelist profiler extension can verify only approved accounts exist on systems, as codified in an authorized user whitelist.Tripwire can ensure that default accounts are disabled and/or passwords are changed where required, and activity logging can provide alerting on inappropriate use of such accounts. Tripwire can verify configuration settings for passwords and other security settings to meet and maintain compliance requirements.Tripwire can verify configuration settings for passwords and other security settings to meet and maintain compliance requirements. Tripwire can verify configuration settings for passwords and other security settings to meet and maintain compliance requirements, and provide alerting when success/failure thresholds are exceeded. |
| CIP-008: Incident Reporting and Response Planning | ||
| CIP-008 R1: Cyber Security Incident Response Plan | Each Responsible Entity shall document one or more Cyber Security Incident response plan(s) that collectively include each of the applicable requirement parts in CIP-008-5 Table R1 – Cyber Security Incident Response Plan Specifications.
|
Tripwire reporting on logs, events, configuration and change detection would help to create IOC reports that could be part of an ISAC response document. |
| CIP-008 R2: Cyber Security Incident Response Plan Implementation and Testing | Each Responsible Entity shall implement each of its documented Cyber Security Incident response plans to collectively include each of the applicable requirement parts in CIP-008-5 Table R2 – Cyber Security Incident Response Plan Implementation and Testing.
|
|
| CIP-008 R3: Cyber Security Incident Response Plan Review, Update, Communication | Each Responsible Entity shall maintain each of its Cyber Security Incident response plans according to each of the applicable requirement parts in CIP-008-5 Table R3 – Cyber Security Incident Response Plan Review, Update, and Communication.
|
|
| CIP-009: Recovery Plans for BES Cyber Systems | ||
| CIP-009 R1: Recovery Plan Specifications | Each Responsible Entity shall have one or more documented recovery plans that collectively include each of the applicable requirement parts in CIP-009-5 Table R1 – Recovery Plan Specifications.
|
Tripwire products can be customized to create baselines for products and devices configuration. These may be called for and used for recovery steps taken after incidents of system attack or failure.
Tripwire products can be customized to create baselines for products and devices configuration. These may be called for and used for recovery steps taken after incidents of system attack or failure. Tripwire products can be used to collect and aggregate logs and event information from a variety of sources. This information can be stored and later used for recovery steps taken after incidents of system attack or failure. |
| CIP-009 R2: Recovery Plan Implementation and Testing | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, its documented recovery plan(s) to collectively include each of the applicable requirement parts in CIP-009-5 Table R2 – Recovery Plan Implementation and Testing.
R2.1. Test each of the recovery plans referenced in Requirement R1 at least once every 15 calendar months:
|
Tripwire products can be customized to create baselines for products and devices configuration. These may be called for and used for recovery steps taken after incidents of system attack or failure.
Tripwire products can be used to collect baselines, logs and event information from a variety of sources. This information can be stored and later used for recovery steps taken after incidents of system attack or failure. |
| CIP-009 R3: Recovery Plan Review, Update and Communication | Each Responsible Entity shall maintain each of its recovery plans in accordance with each of the applicable requirement parts in CIP-009-5 Table R3 – Recovery Plan Review, Update and Communication.
|
|
| CIP-010: Configuration Change Management and Vulnerability Assessments | ||
| CIP-010 R1: Configuration Change Management | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented processes that collectively include each of the applicable requirement parts in CIP-010-1 Table R1 – Configuration Change Management.
|
Tripwire Configuration Assessment Policy and Change audit features can address the creation of a baseline configuration of computer systems and alert and report on change - supporting the process of formal change control and testing.
Tripwire Configuration Assessment Policy and Change audit features can address the creation of a baseline configuration of computer systems and alert and report on change - supporting the process of formal change control and testing. Tripwire supports the tracking and authorization of change to system baseline and configurations - following the process defined by NIST for POA&M reportingTripwire supports the tracking and authorization of change to system baseline and configurations - following the process defined by NIST for POA&M reporting Tripwire reports on security controls deployed, configured and operational status. This reporting will support this requirement.Tripwire baseline comparison operations can verify that a given test environment accurately reflects the production systems. |
| CIP-010 R2: Configuration Monitoring | Each Responsible Entity shall implement, in a manner that identifies, assesses, and corrects deficiencies, one or more documented processes that collectively include each of the applicable requirement parts in CIP-010-1 Table R2 – Configuration Monitoring.
R2.1. Monitor at least once every 35 calendar days for changes to the baseline configuration (as described in Requirement R1, Part 1.1). Document and investigate detected unauthorized changes. |
Tripwire's core functionality offers exceptional change detection and investigation capabilities.
Tripwire Enterprise's core functionality offers exceptional change detection and investigation capabilities. |
| CIP-010 R3: Vulnerability Assessments | Each Responsible Entity shall implement one or more documented processes that collectively include each of the applicable requirement parts in CIP-010-1 Table R3– Vulnerability Assessments.
|
Tripwire IP360 offers excellent vulnerability assessment and reporting across a broad variety of asset types.
Tripwire IP360 offers excellent vulnerability assessment and reporting across a broad variety of asset types. Tripwire IP360 offers excellent vulnerability assessment and reporting across a broad variety of asset types. Controls exist to minimize the potential for adverse effects during a scan.Tripwire IP360 offers excellent vulnerability assessment and reporting across a broad variety of asset types. Controls exist to minimize the potential for adverse effects during a scan. Tripwire Enterprise can be used to ensure the test environment is equivalent to the target BCA.SIH reporting can offer very capable analysis and mitigation reports. Can be tailored based on mitigation tools available. |
| CIP-011: Information Protection | ||
| CIP-011 R1: Information Protection |
|
Tripwire can be used to 1) generate evidence for audit of BCA for file system access controls, and 2) identify files used for evidence of compliance, monitoring them for change and retension (according to requirements and reported for auditors and compliance officials.)
Tripwire Change Auditing feature can be custom configured to assess if an application or operating system is configured for secure data transmission, storage or event logging - itself logging when these settings are changed or suppressed. This feature could support the appropriate management of BES information protection. |
| CIP-011 R2: BES Cyber Asset Reuse and Disposal | Each Responsible Entity shall implement one or more documented processes that collectively include the applicable requirement parts in CIP-011-1 Table R2 – BES Cyber Asset Reuse and Disposal.
|
|
Note 1: Some of the above capabilities require assistance via a Tripwire Professional Services engagement to properly deliver, configure and deploy. Note 2: Indicates which Tripwire products and features are required for this capability: TE FIM: Tripwire Enterprise File Integrity Monitoring TE SCM: Tripwire Enterprise Security Configuration Management TE WLP: Tripwire Enterprise White List Profiler TLC: Tripwire Log Center IP360: Tripwire IP360
HIPAA Compliance for IT with Tripwire:
Securing Personal Health Information
The Health Insurance Portability and Accountability Act (HIPAA) was implemented to protect the confidentiality and integrity of electronic personal health information. Being HIPAA IT compliant means virtual and physical configurations — from networks and servers to virtual machines and security infrastructure-must be maintained and assessed against HIPAA policies, and proven in the event of an audit.
The Tripwire solution for HIPAA IT Compliance incorporates best practices for high integrity systems management. A covered entity using Tripwire to meet the requirements of HIPAA creates a system that reduces the time spent fighting fires caused by poor network and data security practices, and enhances the data security of electronic personal health information (ePHI).
Tripwire delivers a comprehensive solution by:
- Allowing you to meet the core intent of HIPAA's integrity controls with file integrity monitoring. Tripwire can be tuned and managed to meet changes in your HIPAA IT compliance environment.
- Addressing each of the requirements in the Security Rules associated with Part 164, Subpart C, Section 164.312 of Title II of the HIPAA.
- Assuring that change is measured and controlled and compliance status is always known.
- Automating the repair of configurations that intentionally or accidentally fall from secure and compliant states.
- Managing policy compliance for HIPAA as well as a variety of security frameworks such as ISO 27001, COBIT and NIST.
ISO 27001 Compliance:
Security is Standard with Tripwire
The code of practice for International Organization for Standardization (ISO 27001) is recognized internationally as a structured methodology for information security and is widely used as a benchmark for protecting sensitive and private information. A widely held opinion is that ISO 27001 is an umbrella over other requirements of law or regulation (such as JSOX, SOX and the Data Protection Directive) or contractual standards (PCI DSS) because it requires companies to review such obligations when assessing risk. Organizations that choose to adopt ISO 27001 compliance also demonstrate their commitment to high levels of information security.
There are 11 major controls required as part of the ISO 27001 compliance standard that comprise best practices in information security. Tripwire covers them all, including:
- Security Policy
- Organization of Information Security
- Asset Management
- Human Resource Security
- Physical and Environment Security
- Communications and Operations Management
- Access Control
- Information Systems Acquisition, Development and Maintenance
- Information Security Incident Management
- Business Continuity Management
- Compliance
NIST 800-53 Compliance:
Tripwire’s Solution for Continuous Monitoring and Risk Management of Federal Information Systems
Special publications from NIST provide guidance to federal agencies around FISMA compliance. NIST SP 800-53 provides guidelines on security controls required for federal information systems. NIST SP 800-37 was recently released to help achieve near real-time risk management through continuous monitoring of the controls defined in NIST 800-53. NIST 800-137 was also released to provide additional guidance that will require automation to extend reporting and monitoring enterprise-wide.
Tripwire delivers continuous and automated monitoring of NIST 800-53 security controls to help government agencies identify and prioritize assets, identify risk threshold, determine monitoring frequency and report to authorizing officials.
Tripwire’s solution for NIST 800-53/FISMA compliance:
- Implements security controls and assesses configurations against NIST 800-53 policy requirements
- Provides automated remediation or remediation guidance of misconfigurations across heterogeneous IT infrastructure
- Continuously monitors IT configurations and detects high-risk changes with prioritized, actionable real-time alerts
- Demonstrates, through real-time dashboards and automated reports, current, historical and trending compliance
- Extracts actionable information from servers, networks and systems to provide forensic analysis and on-demand, auditable proof
PCI:
Reduce the cost of PCI DSS Compliance
The PCI Data Security Standard (PCI DSS) Compliance is a security best practice created to prevent credit card fraud through increased protection of sensitive data. It applies to all companies who hold, process or pass cardholder data. While avoiding the adoption of PCI standards can result in hefty non-compliance fees, business benefits of PCI DSS compliance include operating a more secure network, protection of corporate brand and reputation, and reduced risk of data breaches and network attacks.
Tripwire combines the power of configuration control and file integrity monitoring (FIM) with comprehensive log and security information event management capabilities to truly deliver continuous compliance and unmatched PCI DSS compliance.
Tripwire delivers a comprehensive solution by:
- Addressing 11 of the 12 PCI DSS Compliance requirements, with specific log management and file integrity monitoring in Requirement 10 and 11
- Helping identify settings that are not PCI compliant across your entire IT infrastructure.
- Providing dynamic change intelligence to prioritize changes or events of interest that cause you to drift out of PCI compliance with built-in, real-time configuration control.
- Instantly alerting you to all changes or suspicious events that could take you out of compliance.
- Storing configuration states over time to prove continuous compliance in an audit.
- Automating the repair of configurations that have fallen out of compliance and returning them to a secure and compliant state.
Tripwire Express for PCI DSS Compliance
Tripwire Express offers self-service implementation, one server at a time, providing small retailers a pay-as-you-grow PCI compliance solution that that can be implemented immediately and affordably.
PCI for Retailers
Achieve PCI compliance cost-effectively for your entire retail ecosystem, from point-of-sale systems to backend payment processing.
PCI for Hospitality
Hospitality industry businesses must extend their PCI compliance efforts all the way to the credit card data captured at the front desk.
Watch the PCI Data Security Standard Compliance, Video Series
Watch the 3 part Video Series with Gene Kim and Josh Corman, "Payment Card Industry Data Security Standard Compliance".
SOX Compliance for IT:
Comprehensive, Cost-effective and Risk-based
The Sarbanes-Oxley Act (SOX) requires that all publicly-held companies must establish internal controls and procedures for financial reporting to reduce the possibility of corporate fraud. Being SOX compliant means your entire IT infrastructure—from server and network security to IT practices and operations—must be reinforced and configured to maintain and demonstrate continuous SOX IT compliance in the event of an audit.
Tripwire solutions provide IT with the internal controls necessary to continually collect and protect the sensitive information needed to report evidence of SOX IT compliance. Your SOX audits can now be quick and far less costly.
Tripwire Enterprise delivers your comprehensive solution by:
- Addressing the Acquire and Implement (AI) and Delivery and Support (DS) guidelines of COBIT with out-of-the-box change audit reporting and a library of COBIT configurations.
- Comparing system configurations to “gold systems,” reporting and remediating configuration items that vary from the "golden" standard.
- Identifying authorized and unauthorized changes or suspicious event activity over a period of time.
- Communicating those changes with reports that display trends in the effectiveness of and adherence to change process controls.
- Providing industry standards and benchmarks to automatically assess configurations, and determining the degree of risk for operational, regulatory and security vulnerabilities.
- Continuously maintaining a known and trusted state by establishing a secure baseline against which to measure change, and then automating the repair of configuration items if they fall out of compliance.
COBIT
The Control Objectives for Information and related Technology (COBIT) framework helps organizations get the most value from their technology investments by providing guidance for IT governance and controls, portions of which focus on the delivery and support aspects of information systems. Tripwire Enterprise incorporates the COBIT framework through custom configuration assessment profiles that organizations can use to achieve and maintain compliance with those sections.



