
Tripwire IT Security and Risk
Tripwire Security Controls Protect Your Data and Reduce Risks

Overview:
With today’s threat landscape it’s a given that your IT infrastructure will be attacked with attempts to steal your sensitive data. It’s what you do to prepare for these attacks and respond to successful ones that makes all the difference.
The Tripwire VIA platform shores up defenses against threats, provides visibility and context into your infrastructure, helps you focus corrective efforts on the events that matter, and lets you operationalize security. With Tripwire, you prevent breaches from occurring—and protect the business when they do—to minimize their consequences.
SANS 20 CSC:
Reducing Risk with SANS 20 CSC
Many organizations face the challenges and increasing threats to their cybersecurity by strategically choosing a security controls framework as a reference for initiating, implementing, measuring and evaluating their security posture as well as managing risk. Over the years, many security control frameworks have been developed (e.g. NIST, ISO/IEC), with the common goal of offering combined knowledge and proven guidance for protecting critical assets, infrastructure and information.
Security controls themselves are technical safeguards and operational procedures that strengthen defenses against threats. They typically require the triad of people, process, and products.
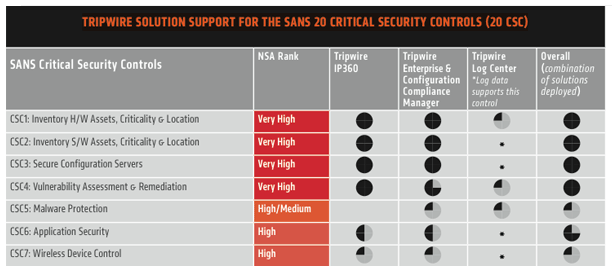
The SANS 20 Critical Security Controls is a prioritized list designed to provide maximum benefits toward improving risk posture against real-world threats. This list of 20 control areas grew out of an international consortium of U.S and international agencies and experts, sharing from actual incidents and helping to keep it current against evolving global cybersecurity threats. Additionally, the SANS Top 20 CSC are mapped to NIST controls as well as NSA priorities.
Tripwire's solutions help organizations of all sizes and types quickly address the first four, truly foundational, security controls. Conquering the first four then lays the foundation for addressing additional controls—which Tripwire can also help with. Using Tripwire, enterprises can achieve accelerated progress on:
- CSC 1 - Inventory of Authorized and Unauthorized Devices
- CSC 2 - Inventory of Authorized and Unauthorized Software
- CSC 3 - Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
- CSC 4 - Continuous Vulnerability Assessment and Remediation
Regardless of the security control framework your organization may be considering or has begun to implement, the SANS 20 is a flexible starting point, applicable to nearly any organization regardless of size, industry, geography or government/commercial. See how Tripwire can help you make rapid progress in establishing a strategy, quickly implementing and then measuring and reporting against your organization's goals.
Vulnerability Management:
Enterprise Vulnerability Management
Vulnerability management is the current evolution from early vulnerability assessment systems that labored to find vulnerabilities, creating reams of data for IT teams to wade through. Today's threat environment is unimaginably different—with thousands of new vulnerabilities reported annually—the sheer volume of launched attacks demands best-in-class vulnerability management solutions to deliver comprehensive discovery that supports the entire vulnerability management lifecycle.
Up-to-date vulnerability management is critical, especially as the time between vulnerability discovery and the release of an exploit is, in some cases, narrowing to zero. Evolving technology constantly increases attack vectors into enterprises and unmanageable numbers of vulnerabilities and required patches means continuous monitoring and remediation is key to enterprise security.
Tripwire's proactive vulnerability management solutions discover comprehensive endpoint and network intelligence and applies advanced analytics to prioritize vulnerabilities in a meaningful framework- flagging the greatest risks so security teams can make quick, quality decisions within a rapidly changing threat landscape.
The Top Choice for Enterprise Networks
The Tripwire IP360 vulnerability management solution provides unique benefits:
- Industry-leading application and vulnerability discovery of all network assets
- Scalability to the largest networks in the world
- Integration with existing IT systems for maximum coverage and minimal operational disruption
- Deployment at customer location, as a cloud-based service, or in combination, for maximum flexibility and value
Exclusive Vulnerability Coverage Guarantee
Tripwire provides the most timely vulnerability intelligence through the company's Vulnerability and Exposure Research Team (VERT), dedicating world-class security and vulnerability researchers, a state-of-the-art lab and unwavering attention to the changing threat environment. Tripwire's VERT identifies emerging vulnerabilities, creating unique detection signatures that are constantly updated in Tripwire vulnerability and risk management solutions- delivering unprecedented vulnerability discovery coverage.
VERT protects Tripwire customers with an exclusive 24-hour Microsoft Security Advisory Service Level Agreement. The Tripwire guarantee: Within 24 hours of a Microsoft advisory, Tripwire IP360 is updated with the signatures to find those vulnerabilities. This guarantee is unique in the industry-only offered by Tripwire to its customers.
VULNERABILITY MANAGEMENT / ASSESSMENT FAQS
What is a vulnerability?
A vulnerability is a software defect or system misconfiguration that allows an attacker to gain increased access or interfere with system operations. Examples include software buffer overflows, or old, unpatched versions of software.
WHAT IS VULNERABILITY ASSESSMENT (VA)?
Vulnerability Assessment is the process of scanning networked devices and discovering vulnerabilities before hackers can exploit them. Tripwire IP360 performs vulnerability assessment as part of the Vulnerability Management lifecycle.
WHAT IS VULNERABILITY MANAGEMENT (VM)?
Vulnerability Management is a closed-loop workflow that generally includes identifying networked devices, auditing (scanning) the devices for vulnerabilities, and remediating the vulnerabilities. Tripwire IP360 is the world’s leading vulnerability management system in use at over 6,500 enterprises worldwide.
HOW IS THIS DIFFERENT FROM PENETRATION TESTING (PEN TESTING)?
Pen testing is a manual security assessment of a network that utilizes vulnerability assessment tools and others to determine network weaknesses. Tripwire partners utilize Tripwire IP360 when conducting penetration tests with their clients.
HOW IMPORTANT IS CURRENT VULNERABILITY COVERAGE?
Up-to-date vulnerability coverage is critical, especially as the window between vulnerability discovery and the release of an exploit is narrows to zero in some cases. Tripwire’s Vulnerability and Exposure Research Team (VERT) produces coverage on the latest vulnerabilities and Tripwire IP360 automatically updates itself as the coverage is released.
WHAT ARE CRITICAL FEATURES OR CAPABILITIES?
Critical features in a VA or VM solution include:
- Scalability – can the solution grow beyond a single department to scan my entire network in a timely fashion?
- Integration – does the solution integrated with other enterprise systems such as ticket systems and IDS/IPS?
- Accuracy and comprehensiveness – does the solution accurately identify networked systems and the vulnerabilities on these systems?
- Modular – can you start small and grow the system to fit your network?
HOW SHOULD I DECIDE BETWEEN USING A MANAGED SERVICE OR ON-PREMISE SOLUTION?
If you desire control over your vulnerability data and integration of the vulnerability data with other systems on your network, an on-premise solution is best for you. If you prefer to outsource your security, a managed service may be an appropriate solution. Tripwire IP360 is the world’s leading on-premise vulnerability management system, and Tripwire partners utilize IP360 to deliver vulnerability management as a service.
HOW DO I GET STARTED WITH VULNERABILITY ASSESSMENTS?
Tripwire makes it easy to get started with auditing your network for vulnerabilities. TripwireIP360’s appliance-based architecture enables you to start small and grow as your network grows.
ARE THERE IMPORTANT METRICS I SHOULD BE TRACKING IN VULNERABILITY MANAGEMENT?
Yes. In order to continually improve your security risk posture, you must measure it using common metrics and compare it to past measurements. Useful VM metrics include:
- Vulnerability score by operating system, application, or organization division – this metric provides a high level measurement of how the organization is doing, cut across several dimensions.
- Most vulnerable applications, with a breakdown into vulnerability score by application version – this metric helps highlight old, vulnerable versions of software that should be upgraded or eliminated.
- Assets scanned within the last “X” days – this metric shows how much of the network is being scanned in a timely fashion.
- Unowned devices and unapproved applications – this metric is very useful to track “unowned” devices that may be rogue devices or simply contractor/consultant systems, as well as the trend of applications that are not specifically allowed on the network.
System State Intelligence:
System State Intelligence (SSI) is the integration of the overwhelming and disjointed information from siloed security controls, which adds context to security events and decreases the time and effort required to identify and respond to security incidents.
SSI provides leading indicators of breach activity by being aware of the state of your systems—how they’re configured and whether they’re configured according to your policy. Once you’ve achieved a known and trusted state, SSI continuously monitors for changes and deviations from your baseline. It detects suspicious events and enables security context and prioritization.
SSI adds immense value to virtually every security solution you have in place. When integrated with SIEM products, it provides a better starting point for incident detection and analysis by reducing false positives and making it less likely to miss a critical security breach.
Security Analytics:
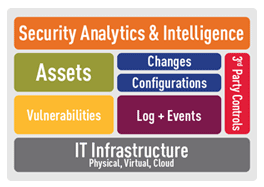
Turn Security Data Into Business Intelligence
Information security is no longer about simply finding breaches. It’s about assessing your organization’s security posture, establishing security goals and then driving your teams to meet them. Security professionals need a way to integrate, transform and visualize disparate sources of security data that helps them support key business assets, services and initiatives.
Tripwire’s solution to security analytics is built on our deep understanding of IT assets, system configurations and vulnerabilities, changes and log events. We integrate this security data with data from third-party controls to transform it into meaningful, actionable information that is presented in the context of the business. Tripwire delivers a comprehensive solution that:
- Gains visibility and context from across the infrastructure by dynamically tagging and associating IT assets
- Detects and integrates critical security control data including configuration, vulnerability, change, incident and log data
- Transforms raw data from your security controls into business intelligence by visualizing system security state in conjunction with business context to help make informed decisions
System Hardening:

Hardened Systems Are Confidence Builders
Consistent, continual IT security hardening is your enterprise’s most valuable security control. It minimizes network vulnerabilities, reduces the attack surface, and helps your organization avoid becoming a victim of zero-day exploits. Yet most security solutions simply try to limit outside access to the system where your sensitive data resides. This perimeter-centric approach to security leaves your infrastructure vulnerable to attack and compromise.
In addition, many IT security regulations require consistency and documentation of security hardening efforts—whether you apply your own IT security hardening policies or depend on the various best practices available from industry sources like COBIT, the Center for Internet Security or NIST. You need a security configuration management solution that reduces the attack surface by applying consistent, continual and automated system hardening. Visit the Tripwire Enterprise Policy Manager page for more information.
But once you've hardened your critical systems and put them under constant watch to combat configuration drift, how do you use this “hardened state” as an objective measure of your overall security posture? How do you report on it in a context the business understands and can relate to? Simple: by transforming raw “security hardening data” into “business intelligence” with the Tripwire VIA Data Mart. Read the datasheet for more information.
| Tripwire delivers Security Configuration Management with Tripwire Enterprise | |
|---|---|
| Security Solution Capability | Why Tripwire? |
| Supplies the industry’s largest security and compliance policy library | Tripwire provides over 20 unique, industry-trusted policy sources, over 250 policy-platform combinations, and over 189,000 unique configuration tests. All are available out-of-the-box, without customization, ready to use. |
| Provides continuous monitoring of a hardened, secure state | Tripwire Enterprise proactively identifies when your critical systems deviate from a known and trusted state to ensure that they remain continuously protected and secure. |
| Adds intelligence to enterprise-wide risk, security and compliance initiatives | Tripwire is the trusted source for information about your infrastructure’s security state. We make it simple and easy to review and understand security hardening data in your executive dashboards and enterprise reports. |
| Supports customized hardening policies for your internal IT security standards | With Policy Manager, you can establish custom weighting for test scores, create scoring thresholds, and determine which results from policy tests need to be flagged and examined. With fully customizable security policy tests, you can turn industry-standard policies into a custom security policy that fits your specific needs. |
Continuous Monitoring:

Continuous Diagnostics & Mitigation
Federal Agencies Depend on Tripwire
Continuous diagnostics & monitoring (also known as continuous monitoring) is not a single solution—it’s a best practice for cybersecurity that government standards, risk-based security frameworks, and compliance mandates require or recommend. Tripwire’s solution for Continuous Diagnostics & Mitigation (CDM) helps agencies reduce their risk by 80%+ in the first 12-18 months. Tripwire maintains a nonstop security profile, transforming historically static security control assessment process, into an automated security information collection process, enabling continuous risk assessment and compliance.

Tripwire solutions fulfill all CDM requirements set forth by the Department of Homeland Security and have been successfully deployed in many government agencies to provide a comprehensive view of all assets within 72 hours or less.
INSTALL & UPDATE SENSORS
- Discover and profile every asset on your entire network for situation awareness
- Fast deployment, automated maintenance, and rapid return on investment
AUTOMATED SEARCH FOR FLAWS
- Detailed asset profiling enables fully automated detection of vulnerabilities and misconfigurations
- Extremely low false positive findings to enable better decision making
COLLECT RESULTS FROM DEPARTMENTS AND AGENCIES
- Supports command & control at the agency, department and/or program level
- Highly scalable solution for comprehensive enterprise coverage
TRIAGE AND ANALYZE RESULTS
- Identifies and prioritizes risks based on exploitability of vulnerabilities and configurations along with numerous customer-specific risk drivers like location; sensitivity; etc.
- Quickly identify good vs. bad changes across the infrastructure to identify potential threats, increase availability, and demonstrate continuous compliance
FIX WORST FIRST
- Granular risk scoring methodology for every finding drives stack-ranked results for prioritized actions
- Deep system integrity technology to help differentiate between good and bad change, reduce configuration drift and focus on changes that matter
REPORT PROGRESS
- Robust APIs support future integration to CDM dashboard
- Quantitative results demonstrate progress to Executives today by showing results and trends by asset, network, organizational components, C&A systems or other agency groupings
Incident Detection:

Detect leading indicators of breach activity early
Cyber attacks, by their very nature, constantly evolve. Old-school reliance on detecting known bad behavior clearly doesn’t work in this age of cyber warfare. Your security strategy has to quickly detect incidents and respond to threats—even the ones that nobody knows about (yet)—to contain system damage and safeguard data. A big part of doing that is seeing threats and anomalous patterns in spite of the vast amounts of data that alerting systems produce. Tripwire’s integrated solutions deliver foundational security controls that can detect leading indicators of breach activity, prioritize detected threats to keep limited resources focused and continuously monitor how well you are managing your attack surface for prevention.
| Tripwire delivers security confidence | |
|---|---|
| Security Solution Capability | Why Tripwire? |
| Quickly detects incidents and lets you immediately respond to threats | Tripwire Log Center provides advanced correlation, intelligent visualization and trend analysis of log data to detect security threats and mitigate risk. |
| Integrated Foundation security controls | Tripwire’s suite of integrated, foundational security controls brings together policy configuration assessment, change auditing, vulnerability assessment, asset business context, and log and event management. This adds unprecedented context of suspicious changes to the security events that are ultimately sent to your security operations team or their security intelligence solution. |
| Provides all necessary information for your security forensics investigations | Easy-to-use search capabilities that yield accurate, comprehensive results let you quickly investigate suspicious incidents and attacks, including their root cause, impact and ongoing effects. |
| Monitors and analyzes the state of your system | Tripwire Enterprise includes file integrity monitoring (FIM) that can be used as a host-based intrusion detection system (HIDS). Use it to detect changes to files, folders and the state of your systems Tripwire IP360 delivers the vulnerability state of your assets, which allows powerful correlations to make on-the-fly determinations whether a target is vulnerable to a detected attack. |
| Combines your protection and detection strategies | Tripwire Cybercrime Controls combine key configuration hardening standards with breach detection rules to detect incidents faster. |
| Adds business context to events of interest | Tight integrations between Tripwire Log Center and Tripwire Asset View lets you identify suspicious activity based on criticality, risk and business impact of your most valued assets. |
