
Tripwire Enterprise
End-to-End Security Configuration Management
Click here to jump to more pricing!
Overview:
Nothing is more critical to information security than establishing and maintaining “known and trusted” configuration states for servers, network devices and databases. Even with that achieved, IT networks are porous and constantly shifting. The IT security solutions that protect them need continual connections to businesses that are highly dynamic and changeable.
Tripwire Enterprise is a security configuration management suite whose Policy Management, Integrity Management, and Remediation Management capabilities stand-alone or work together in a comprehensive, tightly integrated SCM solution.
Key Features
Change-triggered Configuration Assessment
- Continuous, real-time protection with broadest platform and policy support of any SCM solution suite, specially built for core data center usage
- Correlate approved changes to changes actually made, providing proof of compliance with IT policies and standards
World's Best File Integrity Monitoring
- Increase operational efficiencies by reducing configuration drift and unauthorized change
- Deep integrity assessment uses ChangeIQ technology to help differentiate between good and bad change
- Integrate with change management ticketing systems for closed-loop change control
Achieve Continuous Compliance
- Proactively harden systems based on compliance requirements
- Prevent audit failures by complying with standards
- Reduce costs by preparing and passing audits quickly
Integrate SCM into IT Security Operations
- Integrate with incident management/SIEMs to enable early breach detection
- Saves time and money for IT Operations with built-in remediation guidance or automated, multi-user remediation workflow
- Integrate with IT governance systems to provide system state intelligence
Visualize and Report SCM Results to Communicate & Mitigate Risks
- Intelligent, automated asset grouping and tagging to transform security control data into business intelligence
- Web-based, multi-user UI allows security to be pushed out to BUs and operationalized
Features:
TRIPWIRE ENTERPRISE ACHIEVES COMMON EVENT FORMAT (CEF) CERTIFICATION
Tripwire Enterprise is now certified as an ArcSight Common Event Format (CEF) solution. In fact, it’s the only CEF-certified solution to provide “system state intelligence”—the stateful combination of critical change and security configuration data— to ArcSight ESM deployments.
TRIPWIRE ENTERPRISE INTEGRATION WITH HP ARCSIGHT ESM
A “SUPER CONNECTOR” FOR FILE CHANGE AND CONFIGURATION STATE DETAILS
SIEMs are the incident detection tool of choice, but as organizations broadly deploy them throughout large distributed networks, IT security teams face a growing challenge: isolating the real threats from the volumes of noise generated by the IT infrastructure. Industry research and practitioners say the best way to reduce that noise is by comparing security events to other trusted sources of security data—specifically, change and configuration data. This added context quickly knocks away volumes of false positives, and helps security teams focus on the events that matter the most.
Tripwire® Enterprise, an industry-leading security configuration management solution, provides end-to-end configuration assessment and file integrity monitoring. It’s also widely used as the “definitive source of truth” for highly detailed file change and configuration state data. We’re talking about changes to key items like configuration files, ports, servers, binaries and executables— the types of changes that tell you if a system can be trusted.
Now that Tripwire Enterprise is an ArcSight CEF-certified solution, you can combine its highly detailed change and configuration data with security event information in ArcSight ESM using a standard communication format. The payoff? Reduced noise and false positives and greatly improved incident detection.
PRE-PROCESSED DATA TO MAXIMIZE ARCSIGHT ESM CAPABILITIES
Tripwire Enterprise pre-processes its change and configuration data with internal rules and data correlation. This pre-processing allows Tripwire Enterprise to include leading indicators and key metadata in the security data it sends to ArcSight—for example, severities, asset- and test-based risk scoring, and alert information. Plus, you can link back to Tripwire Enterprise from the ArcSight ESM and perform detailed, side-by-side analysis of changes to files and configuration items. This added context lets you maximize the capabilities of ArcSight ESM, giving you a jumpstart on distinguishing between data noise and serious threats.
The Tripwire® VIA™ Event Integration Framework (EIF), a workflow component of Tripwire VIA, serves as an ArcSight connector between Tripwire Enterprise and ArcSight ESM. It lets you:
- Leverage Tripwire Enterprise’s trusted agent, system state visibility, and configuration policy analysis capabilities
- Provide critical state change information as a new, defining variable in ArcSight’s SIEM correlation rules
- Augment security events with context from change and configuration data, like new services opened, new users added, suspiciously elevated privileges, and even attribution information on “who” altered these critical system elements
Adding this detailed change and configuration data from Tripwire Enterprise to ArcSight ESM events shows you not just that “something happened,” but exactly what happened. The cross-linking capability between the two systems even shows users detailed, side-by-side comparisons of detected changes and configuration alterations, allowing them to determine root cause or risk.
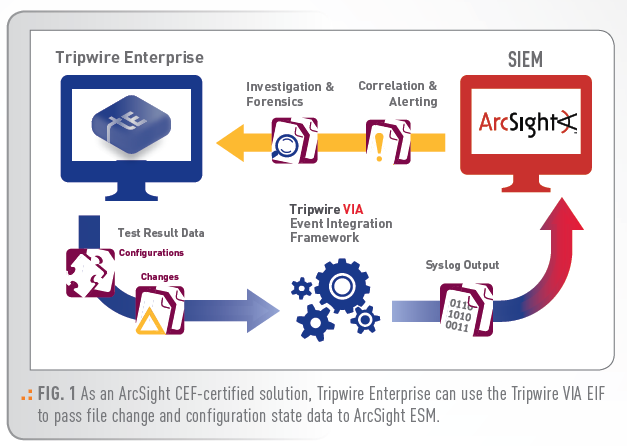
HOW THE INTEGRATION WORKS
- Tripwire Enterprise detects a file state change, or identifies a test failure or score change related to a configuration policy.
- Tripwire Enterprise processes that data using the Tripwire VIA Event Integration Framework.
- Tripwire VIA EIF compiles the data and generates a richly detailed security event message—a “super-event”—to send to ArcSight ESM via Syslog.
- ArcSight ESM normalizes the message and then applies correlation rules to determine the next course of action.
- If the results indicate the need for investigation by the Tripwire Enterprise administrator, details can be incorporated back into Tripwire Enterprise reports and homepages.
A POWERFUL PAIRING FOR INCIDENT DETECTION
ArcSight ESM is the premier SIEM solution in an increasingly threatening world. Tripwire Enterprise is the authority on achieving and maintaining the “known and trusted” state for information security systems, across all platforms and physical and virtual infrastructures.
The integration of the two, using the ArcSight CEF and the Tripwire VIA Event Integration Framework, creates the best of both worlds: an intelligent, scalable, and manageable solution for enterprisewide information security.
| File Change Data | Configuration State Data |
|---|---|
| File changes from baseline | current CI state |
| Severities | Configuration test details |
| Type of changes (content, DACLs, etc.) | Current # and % of pass vs. fail |
| “Who” made the change | Score improvements/declines |
| Deviation from “Known Good” | Change in passes/failures |
| Previous vs. Current deltas | Details of node being tested |
| Number of changes discovered | Numerical change in score |
FIG. 2 Examples of File Change and Configuration State Data Provided by Tripwire Enterprise
Policy Manager:
Security Configuration Management:
Fundamental Security
The SANS Institute for information security lists “secure configurations for hardware and software” as Number Three on its definitive list of “20 Critical Security Controls.” And analyst firm Gartner has shown that security configuration management is the Number One priority in devising a server protection strategy. How can you get this protection?
Tripwire Enterprise’s Policy Manager, a standalone solution or part of Tripwire's SCM Suite, continuously assesses IT configurations against over 300 policies, standards, regulations and vendor guidelines. It's more comprehensive than any other policy management solution, with polices for scores of platforms, dozens of server types, databases and applications, devices and firewalls, in virtual and physical environments. Policy Manager pinpoints non-compliant settings, offers built-in remediation advice, and makes policy status and vulnerabilities not only visible, but actionable.
THE INDUSTRY’S LARGEST POLICY LIBRARY
Tripwire policies come form over 20 unique policy sources—for example, worldwide policies like PCI, CIS and ISO-27001; US-centric policies like NERC, NIST and SOX; and international policies like GPG-13, MAS and ISO-27001. It also supports over 300 policy-platform combinations for operating systems like Windows, Solaris and AIX; databases like IBM DB2, Oracle and MS SQL Server; and numerous application and network devices. It offers over 189,000 unique configuration tests that are ready to use, out of the box—no customization required.
SECURITY DATA TO BUSINESS INTEL: TRIPWIRE DATA MART
Policy Manager’s built-in reports are perfect for users who need to assess their current IT configurations and get them into an audit-passing state. But CISOs and security directors now need to up-level raw security data and convert it into business insight they can share with boards of directors and senior executives. The Tripwire VIA™ Data Mart is an add-on for Policy Manager that converts raw security data from Tripwire Enterprise into business-focused, risk-aligned reports on overall security posture and trends.
Instant Insight: At-a-glance Dashboards
Policy Manager provides dozens of simple and intuitive policy dashboards that can provide instant insight into compliance scores, pass/fail test ratios, compliance trends and summary results. These dashboards can be plugged into custom home pages for any Tripwire Enterprise user on a “role-based access” basis, allowing everyone from CISOs to system administrators to view policy and compliance states.
LINKABLE REPORTS DRILL TO THE DETAILS YOU NEED
Policy reports are easily linked from one report to the next, so users can drill from high-level representations of policy scores right down to the specifics they need. Answer questions like: What test failures combined to make us only 60 percent compliant on this policy? What were the details of the failures? Are there waivers or exceptions in place? Are these failures related to changes detected by Tripwire Enterprise’s File Integrity Manager?
REAL-WORLD MANAGEMENT: WAIVERS AND EXCEPTIONS
Not every configuration item can be tested in a straight pass/fail manner. Systems can be temporarily non-compliant due to upgrades, system status or business processes. Policy Manager allows security managers to create and track waivers to temporarily override failing policy scores, while still flagging these exceptions and noting them in reports and dashboards.
Customizable Policies and Tests
Policy customization allows Tripwire Enterprise users to establish custom weights for test scores, create scoring thresholds and determine which policy test results need to be flagged and examined. With customizable policy tests, IT security teams can customize an industry-standard policy into a security policy that fits their specific needs.
EASY SUPPORT FOR POLICY ACCESS CONTROLS
How do you test a system when you don’t have credentials for it? If your test process does get credentialed, how can you be sure these credentials will be used only as needed? Policy Access Controls allow Tripwire Administrators to establish the right level of access for required tests, while providing visibility to these “keys to the kingdom.”
Remediation Manager:
Automated Security Configuration Remediation Saves Time and Money
Two things plague IT security and operations teams on a daily basis: The time it takes to get new systems into a production-ready state because they must remediate scores of configuration settings before the platform even gets propped up; and the risk that accumulates when configuration items drift from their proper, secure state and stay that ways for days, weeks or even months. Tripwire® Enterprise’s Remediation Manager solves this through an automated, cost-effective system that rapidly restores systems to a secure, compliant state.
A Core Component of the Tripwire Enterprise Suite
Remediation Manager provides a fast, safe way to get new systems into a production-ready, secure state in a fraction of the time it takes using manual methods or even automated deployment scripts. Remediation Manager is the “third leg of the stool,” working with Policy Manager and File Integrity Manager to turn Tripwire Enterprise into an end-to-end security configuration management solution.
Quantifiable Savings in Time and Money
Security activities are often difficult to align with a demonstrable ROI. Many of the things security professionals do are out of self-defense. Not doing them is simply not an option. Remediation Manager, on the other hand, makes a direct and sizeable reduction in the time it takes to prepare or repair configuration settings—a reduction that equates to direct cost savings. As one customer in a 5,000 server environment noted, “We took our Windows 2003 Servers from 47 percent compliance out-of-the-box to 71 percent compliance… in just five minutes.”
Out-of-the-box Integration
Tripwire Enterprise’s Remediation Manager automatically works on the configuration test failures discovered and reported by Tripwire Enterprise’s Policy Manager. To transition from one interface to the other—from assessing to repairing—requires one simple click. Remediation Manager’s dashboard plugs directly into Tripwire Enterprise’s custom home pages, making these capabilities accessible through a familiar interface.
Role-Based Workflows
Change approval is a serious process. “Best practice” frameworks from ITIL to COBIT to ISO-27001 highlight the need to separate duties between those who “assess” policies and those who are allowed to “remediate” the findings and discoveries. Remediation Manager accommodates this through built-in, easy-to-understand, multi-user sign-off processes that make every action traceable and reportable.
Work-Order Based Remediation
Remediation tasks often require IT staff members to work across IT organizational boundaries, which means they also need an intuitive and streamlined way to track and communicate remediation tasks. In Remediation Manager, remediation work orders make it easy to manage various tasks—for example, review, approval, or completion report—as one or more users executes them. These users can easily see and track their responsibilities in personalized instances of the user interface.
Ready-Made Security Configuration Remediation Scripts
Tripwire Enterprise’s Remediation Manager comes with ready-to-use remediation scripts for common configuration test failures across dozens of policies and platforms. These scripts mirror the remediation advice in Tripwire Enterprise’s Policy Manager, providing consistency between remediation tasks undertaken manually and those made using automation.
Extensive Policy Support
Remediation Manager repairs configuration items across a broad array of platforms and policies. Platforms that can be remediated include Windows, Red Hat Enterprise Linux, SUSE Linux, Sun Solaris, AIX and more. Remediation is available for policies across the entire Policy Manager library, from PCI and CIS to DISA, NERC, NIST and many others.
Built-in Remediation Reports
Remediation Manager comes with a pre-built series of reports to trace every aspect of the remediation process, from the original configuration test failure to work order creation, sign offs, and re-tests. Reports can be easily tailored to meet the needs of compliance assessors, operations approvers, or IT security directors.
Specifications:
| PARAMETERS FOR SMALL, INTERMEDIATE AND ENTERPRISE DEPLOYMENTS | ||||||
|---|---|---|---|---|---|---|
| CONFIGURATION | USAGE | CPU | MEMORY | STORAGE | OS | DATABASE |
| Small | Single server installation, small deployments and/or demo systems Shared resources for Tripwire Enterprise and database Low 100s of Agents available on reliable network connections (not remote) Minimal reporting needs (weekly) |
Dual processor/ Quad core | 16GB | 2x7200rpm local | Windows, RHEL & Solaris; 32-bit OK, 64-bit recommended | MySQL acceptable, Microsoft SQL or Oracle recommended. |
| Intermediate | Distributed installation, dedicated database resources High 100s–~5000 Agents on reliable and remote network connections Intermediate reporting needs (several times a week) |
Quad processor/ Quad core | 32GB | 2x10,000rpm local | Windows, RHEL & Solaris; 64-bit required | MySQL not acceptable, Microsoft SQL or Oracle required. |
| Enterprise | Distributed Enterprise installation, dedicated database resources, report federation utilizing Tripwire Data Mart ~5000–10,000+ Agents on reliable and remote network connections Daily reporting needs |
Quad processor/ Six cores | 64GB | 4x10,000rpm local | Windows, RHEL & Solaris; 64-bit required | MySQL not acceptable, Microsoft SQL or Oracle required. |
| DATABASE: CONFIGURATIONS FOR SMALL, INTERMEDIATE AND ENTERPRISE DEPLOYMENTS | ||||||
| CONFIGURATION | CPU | MEMORY | STORAGE | OS | DATABASE | |
| Small | Dual processor/Quad core | 16GB | 2x7200rpm local, 500GB minimum | Windows, RHEL & Solaris; 32-bit OK, 64-bit recommended | MySQL acceptable, Microsoft SQL or Oracle recommended. | |
| Intermediate & Enterprise | Quad processor/Quad core | 16GB | SAN disk array or large direct attached storage (DAS) – IBM, EMC, Network Appliance, BlueArc, etc. At least 12 disks, 15,000rpm Separate LUNs for tablespace |
Windows, RHEL & Solaris; 64-bit required | MySQL not acceptable, Microsoft SQL or Oracle required. | |
NOTE: VIRTUALIZED INSTALLATIONS MUST SATISFY REQUIREMENTS PUBLISHED IN THE TRIPWIRE LARGE-SCALE DEPLOYMENT GUIDE, AND MAY REQUIRE ADDITIONAL TUNING.
Documentation:
Download the Tripwire Enterprise and Arcsight ESM Integration Datasheet (PDF).
- Pricing and product availability subject to change without notice.
